Hello, in this particular article you will provide several interesting pictures of (pdf) security privacy and policy for cryptographic. We found many exciting and extraordinary (pdf) security privacy and policy for cryptographic pictures that can be tips, input and information intended for you. In addition to be able to the (pdf) security privacy and policy for cryptographic main picture, we also collect some other related images. Find typically the latest and best (pdf) security privacy and policy for cryptographic images here that many of us get selected from plenty of other images.
 (PDF) Cryptography Privacy and Security We all hope you can get actually looking for concerning (pdf) security privacy and policy for cryptographic here. There is usually a large selection involving interesting image ideas that will can provide information in order to you. You can get the pictures here regarding free and save these people to be used because reference material or employed as collection images with regard to personal use. Our imaginative team provides large dimensions images with high image resolution or HD.
(PDF) Cryptography Privacy and Security We all hope you can get actually looking for concerning (pdf) security privacy and policy for cryptographic here. There is usually a large selection involving interesting image ideas that will can provide information in order to you. You can get the pictures here regarding free and save these people to be used because reference material or employed as collection images with regard to personal use. Our imaginative team provides large dimensions images with high image resolution or HD.
 Cryptography Policy Template (pdf) security privacy and policy for cryptographic - To discover the image more plainly in this article, you are able to click on the preferred image to look at the photo in its original sizing or in full. A person can also see the (pdf) security privacy and policy for cryptographic image gallery that we all get prepared to locate the image you are interested in.
Cryptography Policy Template (pdf) security privacy and policy for cryptographic - To discover the image more plainly in this article, you are able to click on the preferred image to look at the photo in its original sizing or in full. A person can also see the (pdf) security privacy and policy for cryptographic image gallery that we all get prepared to locate the image you are interested in.
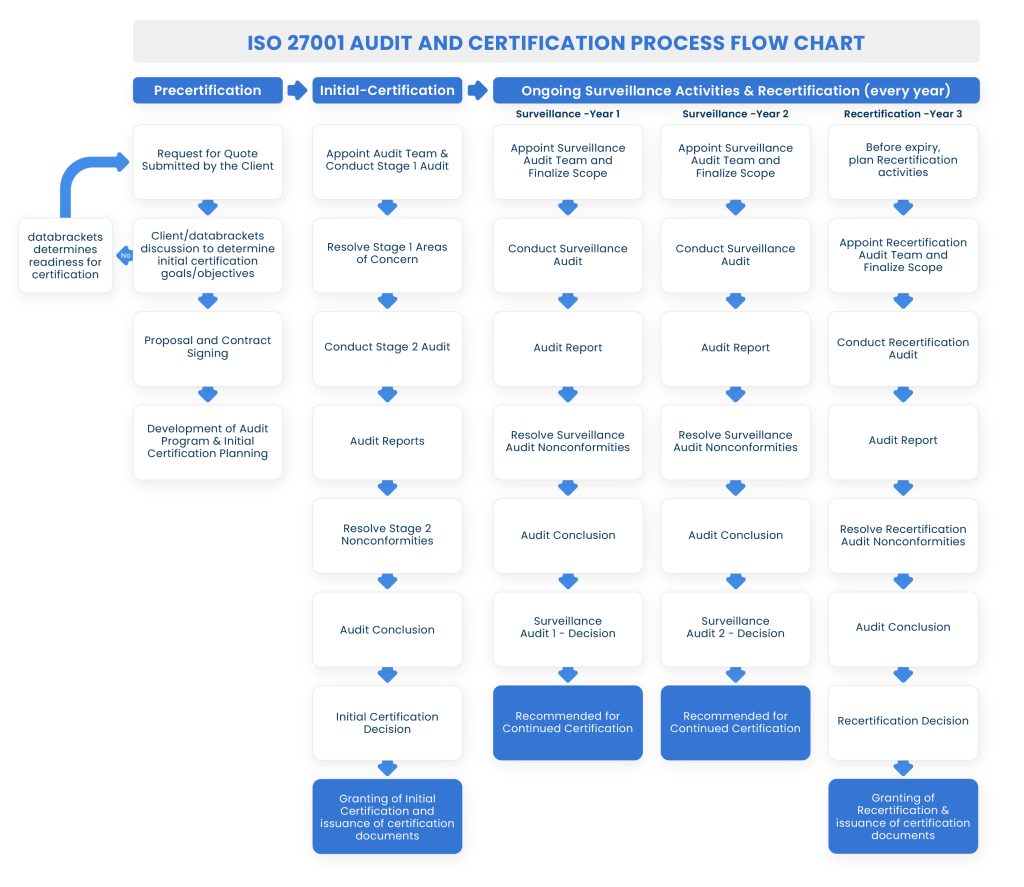 Cryptography Policy Iso 27001 Pdf - Alma Fox Info We all provide many pictures associated with (pdf) security privacy and policy for cryptographic because our site is targeted on articles or articles relevant to (pdf) security privacy and policy for cryptographic. Please check out our latest article upon the side if a person don't get the (pdf) security privacy and policy for cryptographic picture you are looking regarding. There are various keywords related in order to and relevant to (pdf) security privacy and policy for cryptographic below that you can surf our main page or even homepage.
Cryptography Policy Iso 27001 Pdf - Alma Fox Info We all provide many pictures associated with (pdf) security privacy and policy for cryptographic because our site is targeted on articles or articles relevant to (pdf) security privacy and policy for cryptographic. Please check out our latest article upon the side if a person don't get the (pdf) security privacy and policy for cryptographic picture you are looking regarding. There are various keywords related in order to and relevant to (pdf) security privacy and policy for cryptographic below that you can surf our main page or even homepage.
 (PDF) Improving Security in Private Cloud through Cryptographic and Hopefully you discover the image you happen to be looking for and all of us hope you want the (pdf) security privacy and policy for cryptographic images which can be here, therefore that maybe they may be a great inspiration or ideas throughout the future.
(PDF) Improving Security in Private Cloud through Cryptographic and Hopefully you discover the image you happen to be looking for and all of us hope you want the (pdf) security privacy and policy for cryptographic images which can be here, therefore that maybe they may be a great inspiration or ideas throughout the future.

 (PDF) Engineering Cryptography for Security and Privacy in the Cloud The pictures related to be able to (pdf) security privacy and policy for cryptographic in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.
(PDF) Engineering Cryptography for Security and Privacy in the Cloud The pictures related to be able to (pdf) security privacy and policy for cryptographic in the following paragraphs, hopefully they will can be useful and will increase your knowledge. Appreciate you for making the effort to be able to visit our website and even read our articles. Cya ~.
 (PDF) Research on Blockchain: Privacy Protection of Cryptography (PDF) Research on Blockchain: Privacy Protection of Cryptography
(PDF) Research on Blockchain: Privacy Protection of Cryptography (PDF) Research on Blockchain: Privacy Protection of Cryptography
 (PDF) CORROSIVE SECRECY AND CONFIDENCE: THE PARADOX AMONG BYPASSING (PDF) CORROSIVE SECRECY AND CONFIDENCE: THE PARADOX AMONG BYPASSING
(PDF) CORROSIVE SECRECY AND CONFIDENCE: THE PARADOX AMONG BYPASSING (PDF) CORROSIVE SECRECY AND CONFIDENCE: THE PARADOX AMONG BYPASSING
 FREE 13+ Data Security Policy Templates in PDF | MS Word FREE 13+ Data Security Policy Templates in PDF | MS Word
FREE 13+ Data Security Policy Templates in PDF | MS Word FREE 13+ Data Security Policy Templates in PDF | MS Word
 (PDF) Applied Cryptography and Network Security (PDF) Applied Cryptography and Network Security
(PDF) Applied Cryptography and Network Security (PDF) Applied Cryptography and Network Security
 (PDF) Implementation of Cryptography for Privacy Preserving Data Mining (PDF) Implementation of Cryptography for Privacy Preserving Data Mining
(PDF) Implementation of Cryptography for Privacy Preserving Data Mining (PDF) Implementation of Cryptography for Privacy Preserving Data Mining
 (PDF) Privacy Protection of Digital Images Using Watermarking and QR (PDF) Privacy Protection of Digital Images Using Watermarking and QR
(PDF) Privacy Protection of Digital Images Using Watermarking and QR (PDF) Privacy Protection of Digital Images Using Watermarking and QR
 Security, Privacy, and Applied Cryptography Engineering: 4th Security, Privacy, and Applied Cryptography Engineering: 4th
Security, Privacy, and Applied Cryptography Engineering: 4th Security, Privacy, and Applied Cryptography Engineering: 4th
 (PDF) STRIDE: A Secure Framework for Modeling Trust-Privacy Tradeoffs (PDF) STRIDE: A Secure Framework for Modeling Trust-Privacy Tradeoffs
(PDF) STRIDE: A Secure Framework for Modeling Trust-Privacy Tradeoffs (PDF) STRIDE: A Secure Framework for Modeling Trust-Privacy Tradeoffs
 Relationship between privacy, cryptographic-based security and trust Relationship between privacy, cryptographic-based security and trust
Relationship between privacy, cryptographic-based security and trust Relationship between privacy, cryptographic-based security and trust
 (PDF) AN EFFICIENT CRYPTOGRAPHIC APPROACH FOR PRESERVING PRIVACY IN (PDF) AN EFFICIENT CRYPTOGRAPHIC APPROACH FOR PRESERVING PRIVACY IN
(PDF) AN EFFICIENT CRYPTOGRAPHIC APPROACH FOR PRESERVING PRIVACY IN (PDF) AN EFFICIENT CRYPTOGRAPHIC APPROACH FOR PRESERVING PRIVACY IN
 Premium AI Image | Protecting information with cryptographic techniques Premium AI Image | Protecting information with cryptographic techniques
Premium AI Image | Protecting information with cryptographic techniques Premium AI Image | Protecting information with cryptographic techniques
 What is Cryptography? | Cryptographic Algorithms | Types of What is Cryptography? | Cryptographic Algorithms | Types of
What is Cryptography? | Cryptographic Algorithms | Types of What is Cryptography? | Cryptographic Algorithms | Types of
 Lightweight Cryptography for Security and Privacy | 9783319557137 Lightweight Cryptography for Security and Privacy | 9783319557137
Lightweight Cryptography for Security and Privacy | 9783319557137 Lightweight Cryptography for Security and Privacy | 9783319557137
 (PDF) A Privacy Protection Framework for Medical Image Security without (PDF) A Privacy Protection Framework for Medical Image Security without
(PDF) A Privacy Protection Framework for Medical Image Security without (PDF) A Privacy Protection Framework for Medical Image Security without
 Cryptography and Network Security: Principles and Practice (7th Edition Cryptography and Network Security: Principles and Practice (7th Edition
Cryptography and Network Security: Principles and Practice (7th Edition Cryptography and Network Security: Principles and Practice (7th Edition
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab 42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-34.jpg) 42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab 42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab 42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
 UNIT II - NETWORK SECURITY AND CRYPTOGRAPHY UNIT II - NETWORK SECURITY AND CRYPTOGRAPHY
UNIT II - NETWORK SECURITY AND CRYPTOGRAPHY UNIT II - NETWORK SECURITY AND CRYPTOGRAPHY
 (PDF) Security, privacy and freedom 2012 (PDF) Security, privacy and freedom 2012
(PDF) Security, privacy and freedom 2012 (PDF) Security, privacy and freedom 2012
 13+ Privacy Policy Templates | Free PDF Samples, Examples 13+ Privacy Policy Templates | Free PDF Samples, Examples
13+ Privacy Policy Templates | Free PDF Samples, Examples 13+ Privacy Policy Templates | Free PDF Samples, Examples
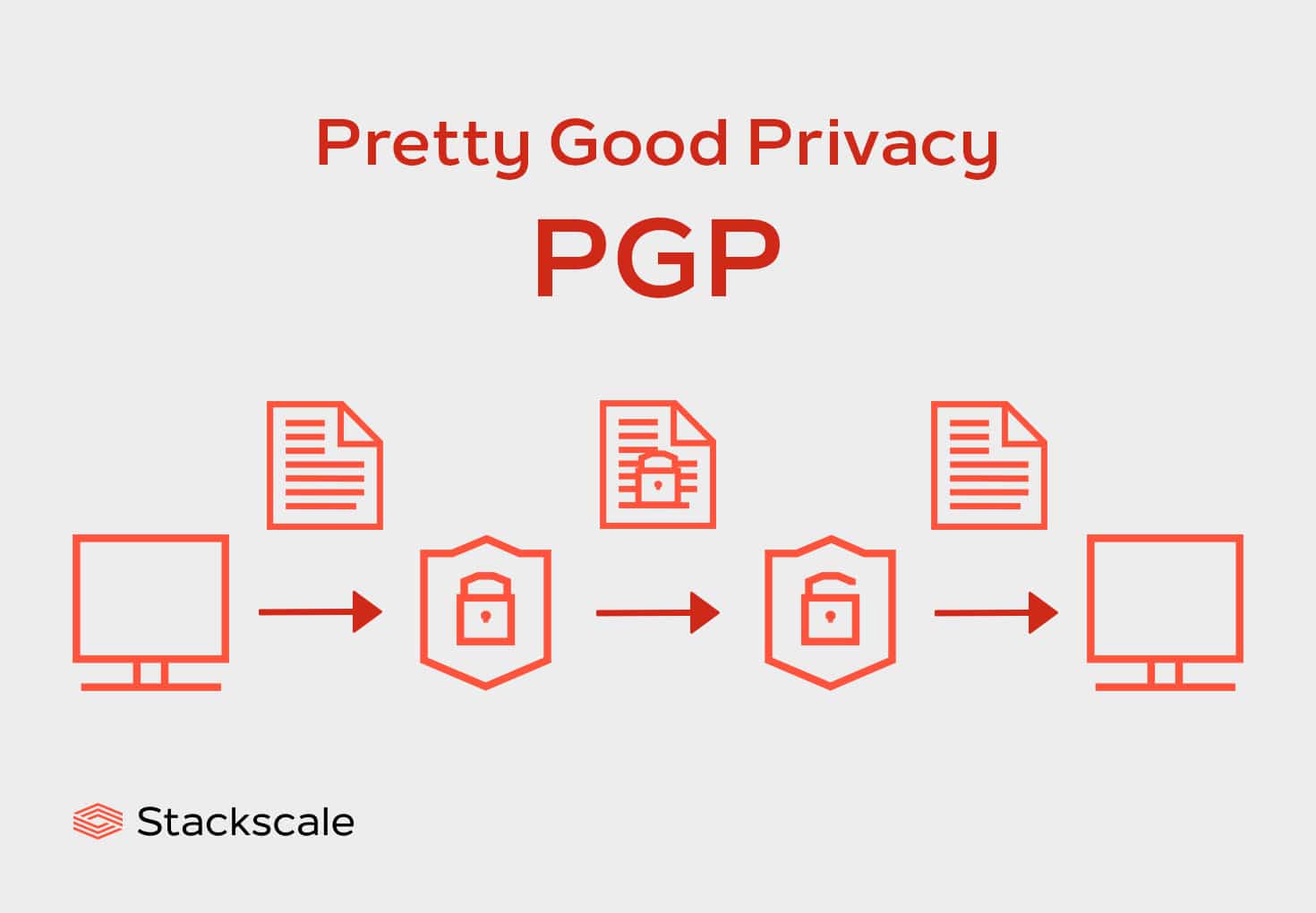 What's PGP or Pretty Good Privacy? | Stackscale What's PGP or Pretty Good Privacy? | Stackscale
What's PGP or Pretty Good Privacy? | Stackscale What's PGP or Pretty Good Privacy? | Stackscale
 Free Privacy Policy Templates (9) & Generator - PDF | Word - eForms Free Privacy Policy Templates (9) & Generator - PDF | Word - eForms
Free Privacy Policy Templates (9) & Generator - PDF | Word - eForms Free Privacy Policy Templates (9) & Generator - PDF | Word - eForms
 Public Key vs Private Key - Public Key Cryptography Explained | Sectigo Public Key vs Private Key - Public Key Cryptography Explained | Sectigo
Public Key vs Private Key - Public Key Cryptography Explained | Sectigo Public Key vs Private Key - Public Key Cryptography Explained | Sectigo
 加密初学者指南。 Beginners Guide to Cryptography - Quick博客 加密初学者指南。 Beginners Guide to Cryptography - Quick博客
加密初学者指南。 Beginners Guide to Cryptography - Quick博客 加密初学者指南。 Beginners Guide to Cryptography - Quick博客
 What is Cryptography? Learn Cryptography and Network Security - Geeks What is Cryptography? Learn Cryptography and Network Security - Geeks
What is Cryptography? Learn Cryptography and Network Security - Geeks What is Cryptography? Learn Cryptography and Network Security - Geeks

